Hosuk Lee-Makiyama / Nov 2019

Image: Shutterstock
Since March this year, the EU Member States have taken concrete steps to support an EU-wide approach to secure 5G networks, starting with a joint risk assessment due to be circulated this month. The report is likely to highlight the Member State views and experiences on assets, threats and vulnerabilities related to 5G infrastructure and form the basis for a “toolbox” for mitigating new risks.
As we have highlighted in several ECIPE reports, 5G unleashes unprecedented benefits, while also exposing the society to new economic, technical and geostrategic threats. Such risks are reasonably isolated in today’s networks by technical means, the complexity of 5G make our networks more vulnerable to human errors, threat actors and design flaws.
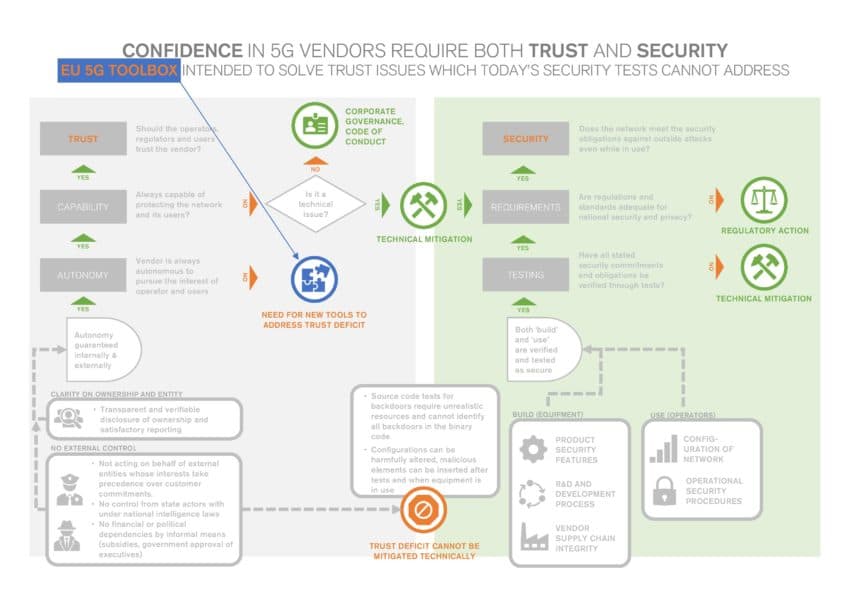
It highlights a renewed question of trust: Are we confident that a vendor will put the interests of operators, users and Europe in forefront – under any condition or every circumstance? Unlike security that can be verified through testing the equipment, trust cannot be “tested” technically.
What’s matured in the European debate is how “security” and “trust” are actually two distinct and separate concepts – and a 5G supplier must tick both boxes. A trust deficit cannot be mitigated by engineers or coders – and sometimes not even by the supplier itself. The new EU toolbox will contain tools to address such situations when trust goes missing.
Some European countries (notably France, the UK, Germany) have taken legislative action under their national laws to deal with the trust deficit issue. Those measures include (and combine), supplier diversification (ban against a vendor establishing a monopoly over a network, or a “monoculture”) or exclusion of unreliable vendors in sensitive geographic areas and parts of the network (such as the core network functions). Yet diversification and partial exclusion merely limit the potential damage from breaches or disruptions, but do not eliminate the risks.
While we are working on a forthcoming publication on the 5G risks, we developed the following schematics to illustrate the distinctions between the problems concerning trust and security and what their differences imply in terms of responsibilities and mitigation methods.